AZURE: Microsoft Sentinel Honeypot & Attack Monitoring Lab
Summary
This project demonstrates the design and deployment of a cloud-based honeynet in Microsoft Azure, integrated with Microsoft Sentinel for real-time attack detection, threat intelligence enrichment, and global telemetry visualization.
A publicly exposed Windows VM was intentionally configured with weakened firewall and network security controls to attract real adversary activity from the internet. Logs were collected using the Azure Monitoring Agent and correlated within Sentinel for threat hunting, mapping attacker geolocation, and building security analytics.
Published on November 20, 2025 by Ewan Oleghe.
Introduction
This hands-on security project focuses on building a realistic Security Operations Center (SOC) home lab using Azure services.
The goal was to:
- Deploy a vulnerable Windows VM on Azure
- Expose it to the internet to attract live attack traffic
- Ingest logs into Log Analytics Workspace
- Enable Microsoft Sentinel to monitor, analyze, and visualize attacker behavior
- Build custom KQL queries, alert rules, dashboards, and watchlists
- Map global brute-force attempts using threat-intel and GEO-IP data
The lab simulates real-world SOC workflows such as threat detection, log analysis, alerting, correlation, and visualization, allowing practical blue-team experience with Azure-native tools.
Introduction
- Set-up a New Azure account or
- Log-in to Azure portal : https://portal.azure.com/
Step 1: Create a Resource Group
The local container that groups everything related to one project (e.g., VM, VNet, NIC, Public IP).
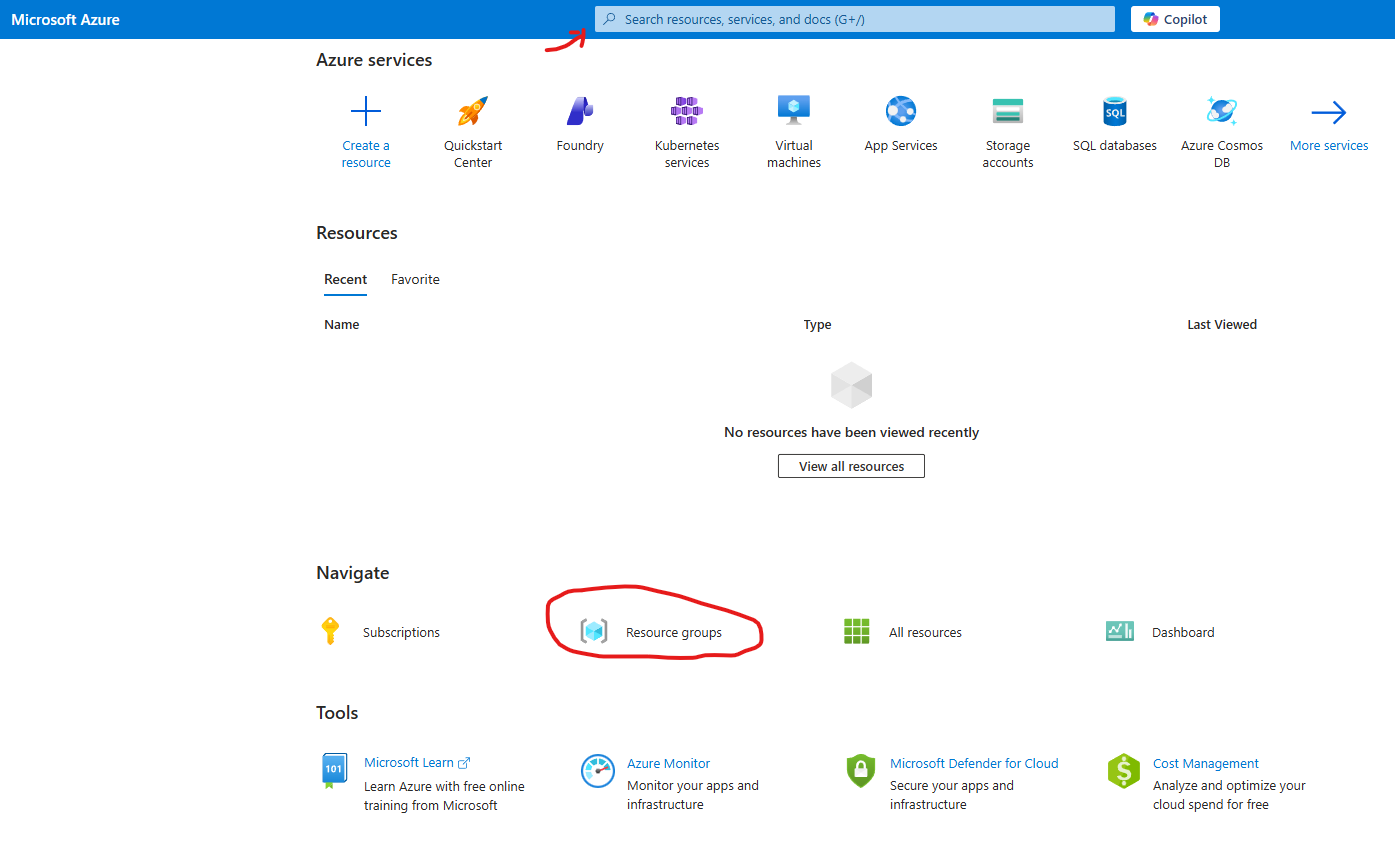
- Use the search bar or
- Select resource Groups in the Navigate section
- Create a Resource group
- Subscription: Select your subscription
- Resource group: Name your resource group (e.g., H-SOC-Lab)
- Region: Select a region close to you (e.g., East US)
- Review and Create
Step 2: Create a Virtual Network (VNets)
The VNets a private, customizable network allows us to connect and secures resources. Our Virtual Machine will be placed inside the Virtual Network
- Use the search bar or
- Select Virtual networks - under Services
- Create virtual network
- Subscription: Select your subscription
- Resource group: H-SOC-Lab
- Virtual network name (e.g., VNet-SOC-Lab)
- Region: Select a region close to you (e.g., East US)
- Review and Create
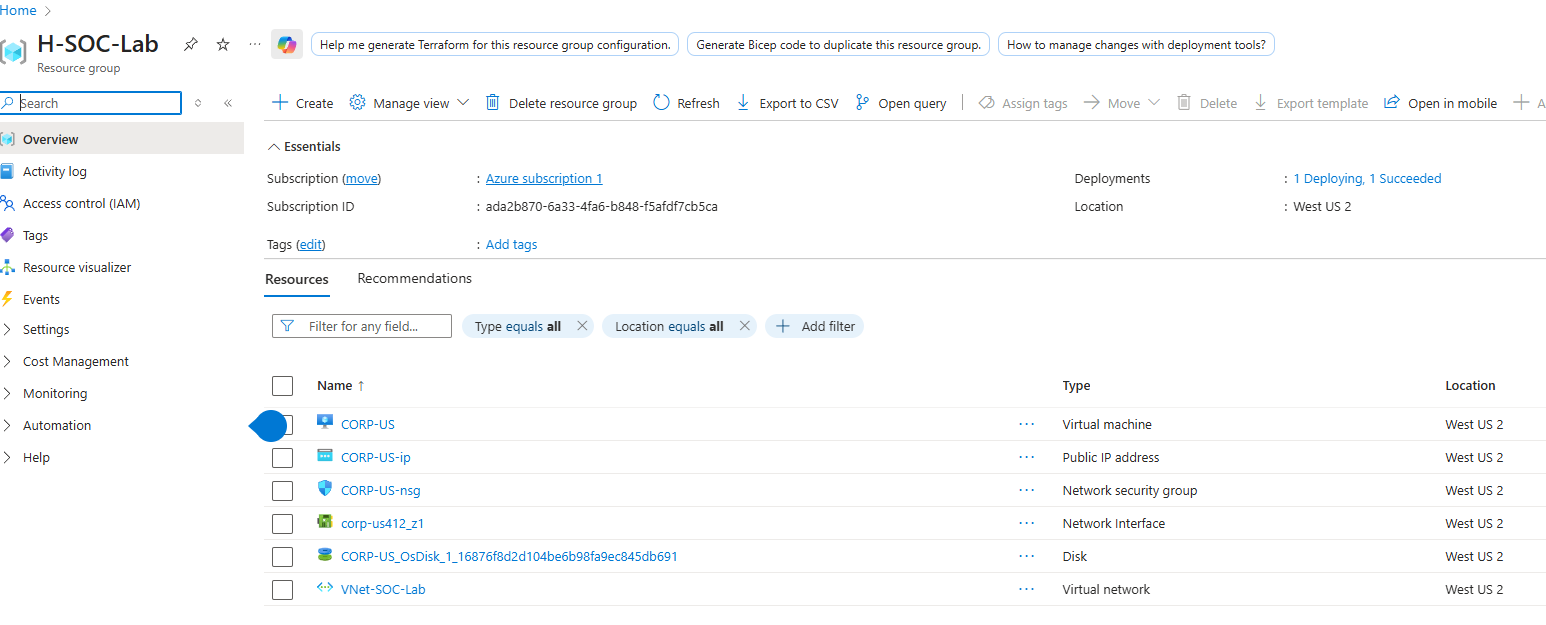
Step 3: Create a Virtual Machine (VM)
In Microsoft Azure, a VM is a cloud-hosted computer - This is what will be exposed to the Internet/attackers.
- Use the search bar or
- From the Home page, Select 'Virtual Machines' in Azure services section
- Create a Virtual Machine
- Select Virtual Machine
- Resource group: H-SOC-Lab
- Virtual machine name: (e.g., CORP-US) - do not use honeypot- attachers can easily resolve the name to the IP
- Region: Select a region close to you (e.g., East US)
- Image: Windows 10 or 11 or any other Windows OS
- Size: (Chose a small machine to manage cost)
- check - confirm I have an eligible Windows 10/11 license
- -> Next: Disk
- OS disk type: Select a small disk or HDD
- -> Next: Networking
- Virtual network: 'VNet-SOC-Lab'
- Subnet: 'default'
- Check: 'Delete public IP and NIC when VM is deleted'
- -> Next: Management
- -> Next: Monitoring
- Boot diagnostics - Check: 'Disable'
- -> Next: Advanced
- -> Next: Review & Create
- -> Next: Create
Step 4: Configure Network Security Group (NSG) Rules
The NSG acts as a virtual firewall to control inbound and outbound traffic to the VM. We will create rules to allow specific traffic to the honeypot VM.
- Inbound Security rules: Delete the default RDP
- Set-up new traffic rule that allows inbound to all protocol
- Go to Settings > Inbound security rules > + Add
- Source: Any
- Source port ranges: * (all)
- Destination: Any
- Service: Custom
- Destination port ranges: *
- Protocol: Any
- Action: Allow
- Priority: 100
- Name: Danger_vm_inboubd
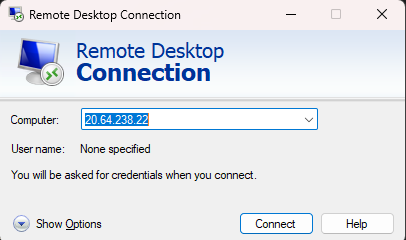
Step 5: Log-in to VM
- RDP
- Log-in to VMM and disable the internal firewall on the VM
- Use RDP to login to the VM
- Primary NIC public IP: 20.64.238.22

- Turn off Windows Firewall
- on the Vm search for 'wf.msc
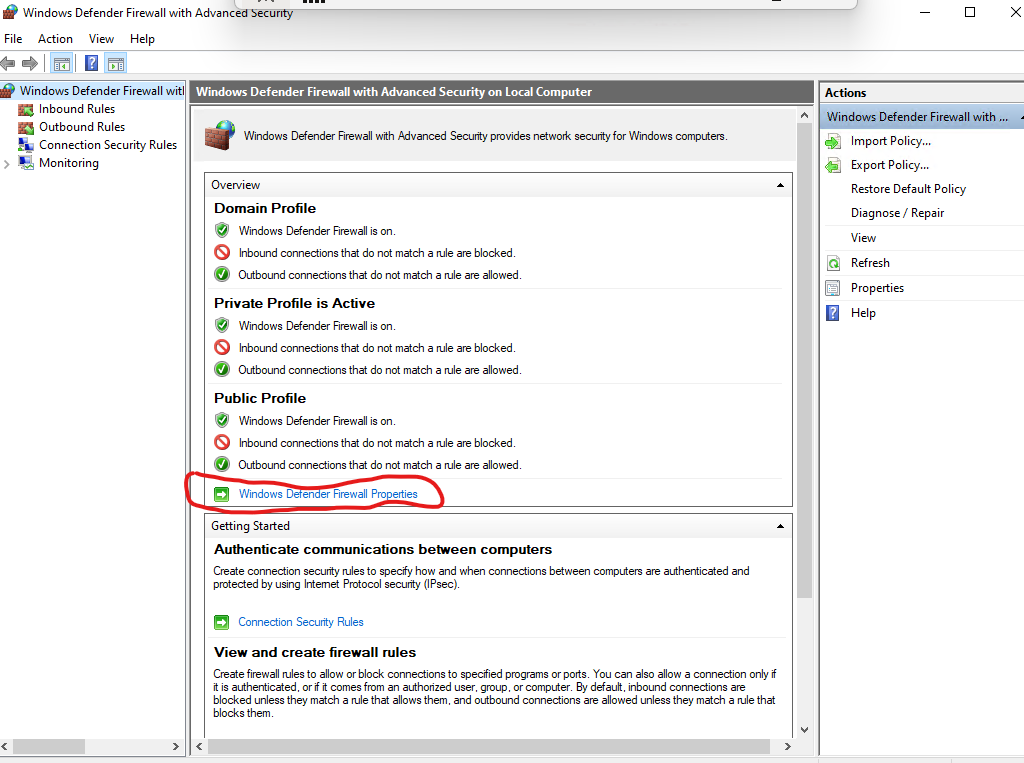
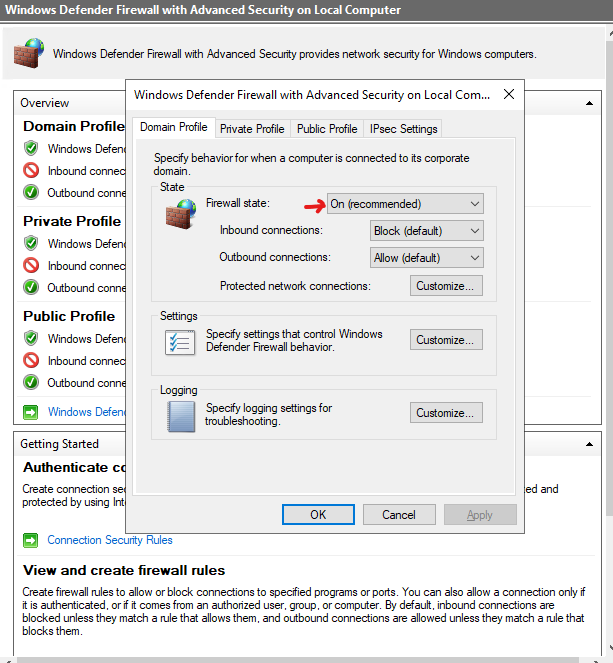
- Click : Windows Defender Firewall Properties and Turn off Firewall for each profile (Domain, Private and Public profiles)
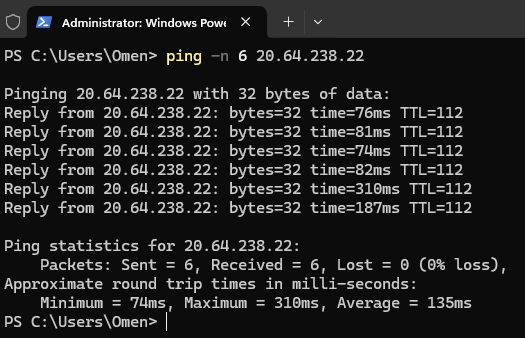
Ping the VM to local Computer
From your local machine. Use CMD or PowerShell to ping the VM. We have to make sure its accessible on the internet.
ping -n 6 20.64.238.22
Pings the VM and a total of 6 packets sent and received
Step 6: Set-up Log Analytics Workspace & Microsoft Sentinel
By default the VM keeps all the Security Events in 'Event Viewer' - Windows Logs - Security.
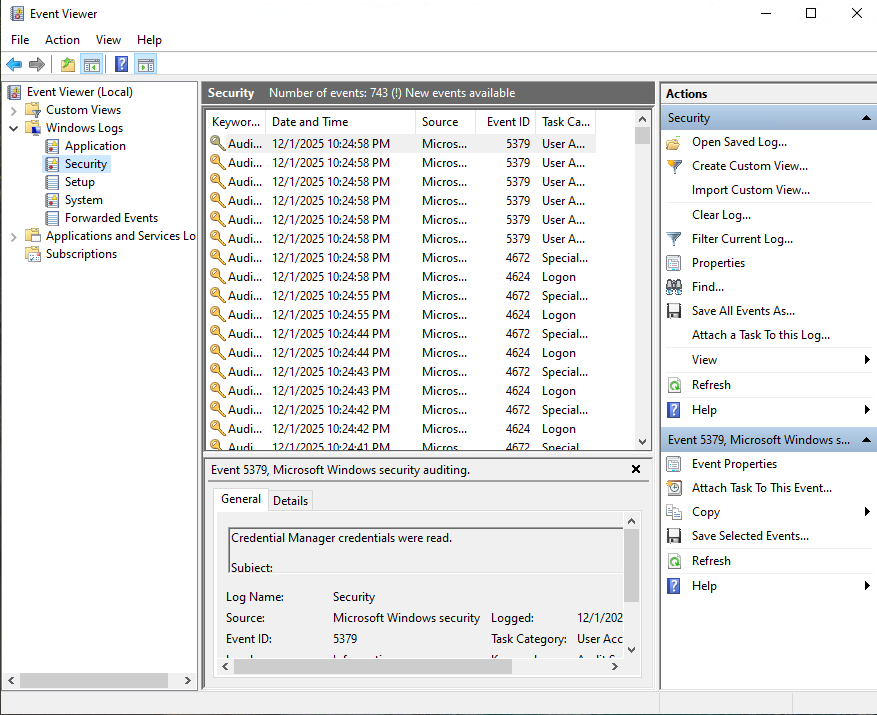
Each ID corresponds to a security events and an ID search can be used to filter logs (e.g. For failed logs search (Ctrl + F or 'Filter current log..') for '4625')
Configure a Log Repository
To collect and analyze these logs in Microsoft Sentinel, we need to set up a Log Analytics Workspace and enable Microsoft Sentinel (SIEM).
- AZURE: Create 'Log Analytics workspace'
- Resource group: H-SOC-Lab
- Name: Log-SOC-lab
- Region: East US 2
- Review & Create
Create Microsoft Sentinel Instance
- AZURE: Create 'Microsoft Sentinel'
- Select the Log Analytics workspace: Log-SOC-lab
- Add
Configure the Connection between VM and Log Analytics
- AZURE: 'Microsoft Sentinel'
- Content Management
- Content Hub
- Search: Windows Security Events
- Select & Install: Windows Security Events
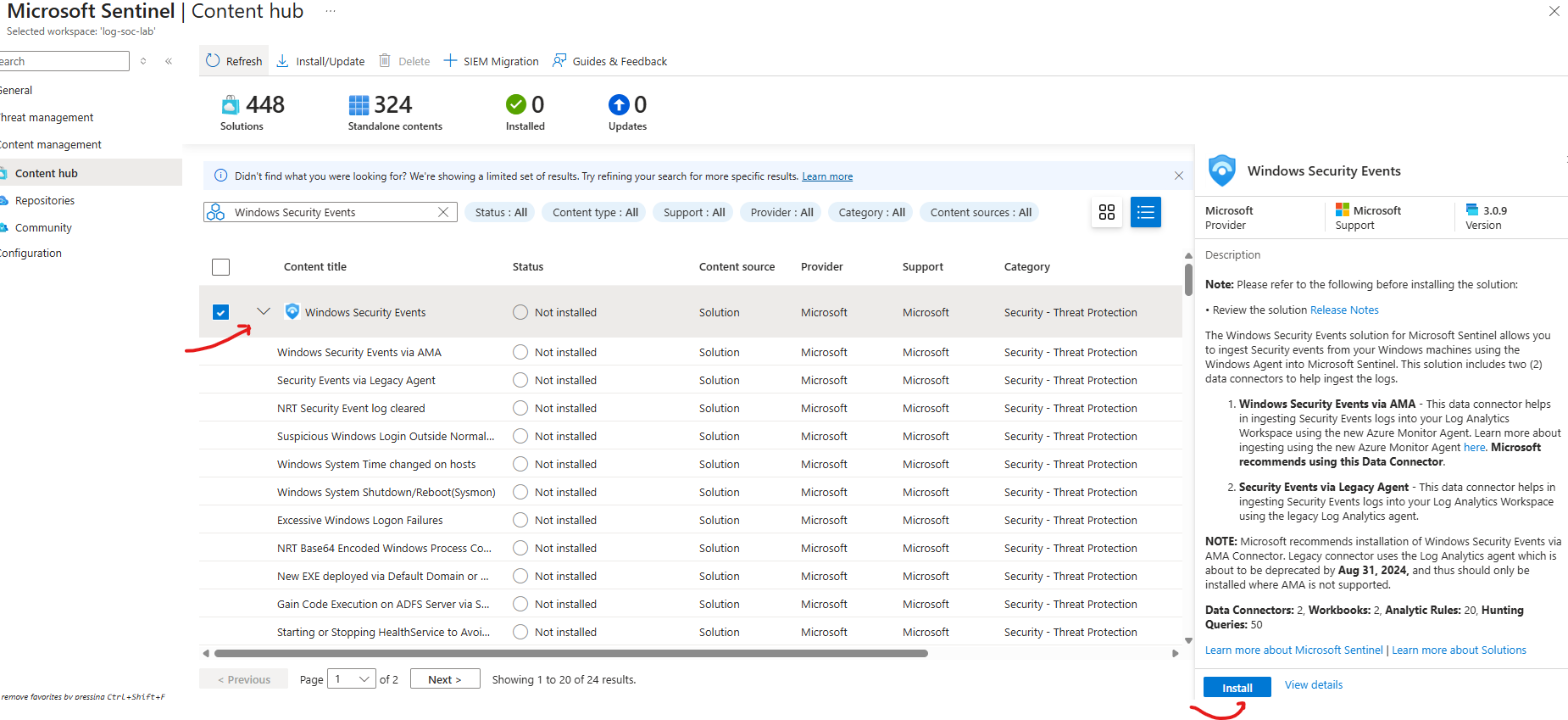
Manage Windows Security Events via Azure Monitoring Agent (AMA)
- AZURE: 'Microsoft Sentinel'
- Configuration
- Click on Manage - Windows Security Events
- Check and Install the Windows Security Events via AMA
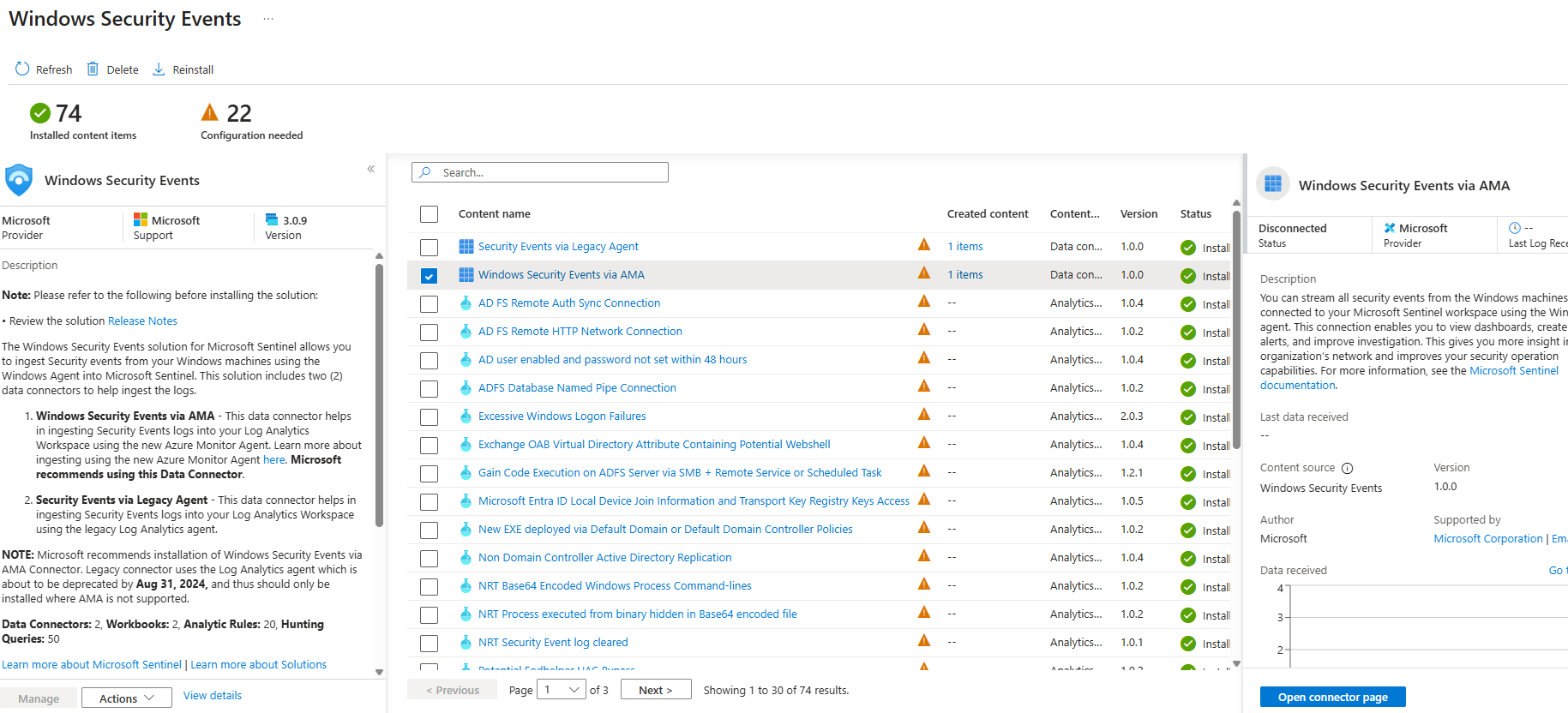
- AZURE: 'Microsoft Sentinel': Windows Security Events via AMA
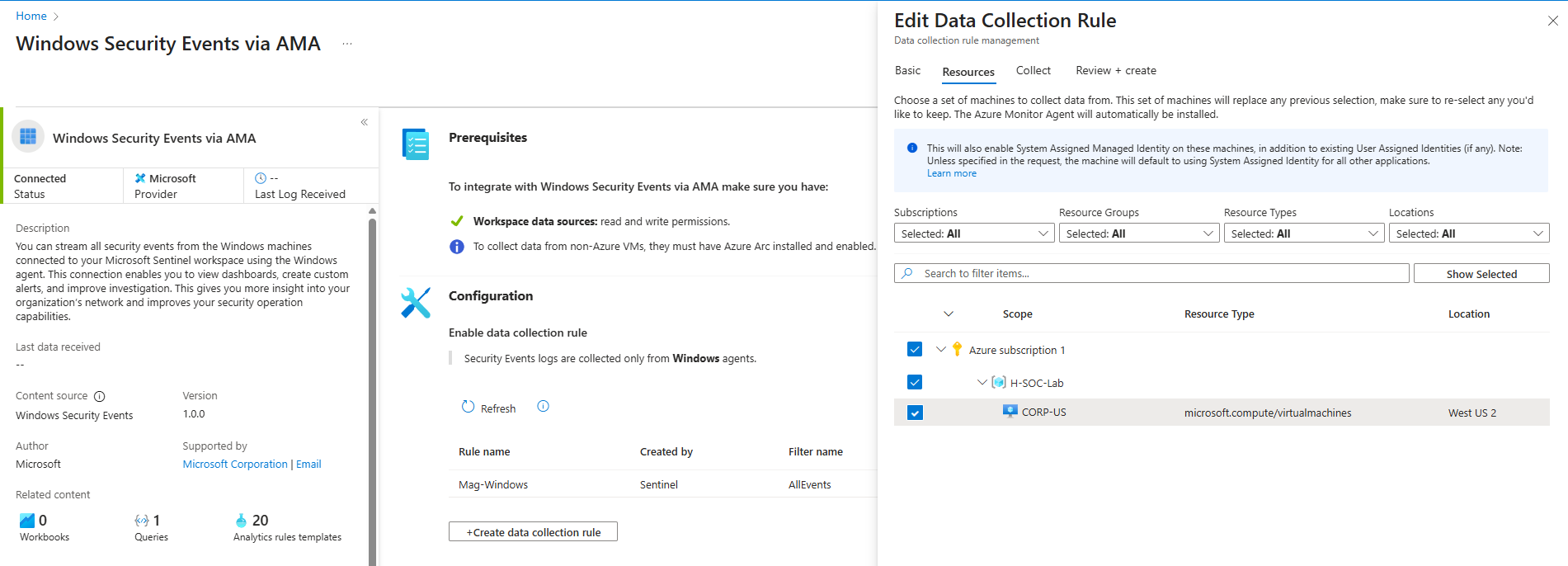
- Open connector page
- +Create data collection rule
- Check and Install the Windows Security Events via AMA
- Configuration
- Rule name: Mag-Windows
- Resource group: H-SOC-Lab
- Next: Resources
- Expand 'Azure Subscription, then RG and select the resource group and VM
- Next: Collect all security events
- Next: & Create
Step 7: Monitor Attacks in Microsoft Sentinel
- AZURE: 'Log Analytics workspaces'
- Select the Sentinel : Log-SOC-lab
- Select: Logs > Table > SecurityEvents
- To Use KQL queries: Logs > Queries > (top right: change from User Mode to KQL mode)
Example KQL Queries to Monitor Attacks
// Failed RDP Log-in Attempts (Event ID: 4625)
SecurityEvent
| where EventID == 4625
| summarize Count = count() by Account, IpAddress, bin(TimeGenerated, 1h)
| order by Count desc
// All RDP Log-in Attempts (Successful and Failed)
SecurityEvent
| where EventID in (4624, 4625)
// Targeted Specific Account e.g. "administrator "
SecurityEvent
| where Account == "\\administrator"
// Top Targeted Accounts by Failed Log-ins
SecurityEvent
| where EventID == 4625
| summarize FailedAttempts = count() by Account
| order by FailedAttempts desc
// Successful RDP Log-in Attempts (Event ID: 4624)
SecurityEvent
| where EventID == 4624
| summarize Count = count() by Account, IpAddress, bin(TimeGenerated, 1h)
| order by Count desc
// Top Source IPs by Failed Log-ins
SecurityEvent
| where EventID == 4625
| summarize FailedAttempts = count() by IpAddress
| order by FailedAttempts desc
| take 10
// Brute-force Attack Patterns
SecurityEvent
| where EventID == 4625
| summarize Attempts = count() by IpAddress, bin(TimeGenerated, 10m)
| where Attempts > 5
| order by Attempts desc
// Geo-location of Attackers
SecurityEvent
| where EventID == 4625
| extend GeoInfo = iplocation(IpAddress)
| summarize Count = count() by GeoInfo.CountryOrRegion
| order by Count desc
Geo-location of Attackers
- Add Geographic Data to resolve IpAddresses to Physical Location
- Import a spreadsheet which contains geographic information for each block of IP addresses (as a "Sentinel Watchlist").
Download: geoip-summarized.csv
- Azure: search: Microsoft Sentinel > select: Configuration > select: watchlist > + New
- Watchlist wizard - General
- Name: geoip
- Alias: geoip
- Watchlist wizard - Source
- Source type: local file
- File type: csv with header
- Upload file: upload the downloaded file 'geoip-summarized.csv'
- SearchKey: network
- Review & Create
_GetWatchlist("geoip")
See where the attacks are coming from
let GeoIPDB_FULL = _GetWatchlist("geoip");
let WindowsEvents = SecurityEvent
| where IpAddress == <attacker IP address> // Replace Ip address "147.91.111.100"
| where EventID == 4625
| order by TimeGenerated desc
| evaluate ipv4_lookup(GeoIPDB_FULL, IpAddress, network);
WindowsEvents
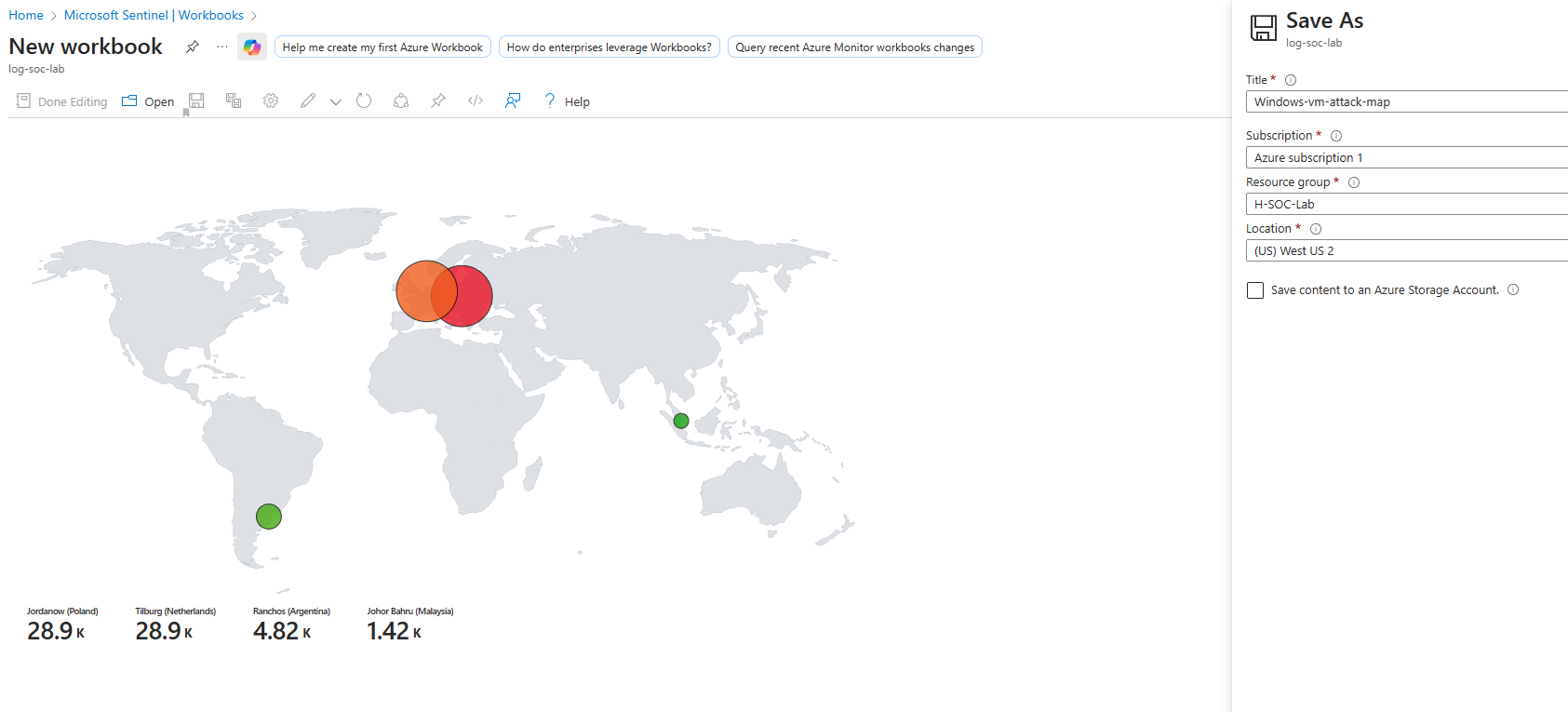
Attack Map Creation
- AZURE: 'Create Sentinel Workbook'
- Select the Sentinel : Log-SOC-lab > Threat Management > Workbooks > + Add Workbook > Edit > (use 3 dots to remove all content)
- Add > add query > Advanced editor (delete and paste the json code below) > Done editing
{
"type": 3,
"content": {
"version": "KqlItem/1.0",
"query": "let GeoIPDB_FULL = _GetWatchlist(\"geoip\");\nlet WindowsEvents = SecurityEvent;\nWindowsEvents | where EventID == 4625\n| order by TimeGenerated desc\n| evaluate ipv4_lookup(GeoIPDB_FULL, IpAddress, network)\n| summarize FailureCount = count() by IpAddress, latitude, longitude, cityname, countryname\n| project FailureCount, AttackerIp = IpAddress, latitude, longitude, city = cityname, country = countryname,\nfriendly_location = strcat(cityname, \" (\", countryname, \")\");",
"size": 3,
"timeContext": {
"durationMs": 2592000000
},
"queryType": 0,
"resourceType": "microsoft.operationalinsights/workspaces",
"visualization": "map",
"mapSettings": {
"locInfo": "LatLong",
"locInfoColumn": "countryname",
"latitude": "latitude",
"longitude": "longitude",
"sizeSettings": "FailureCount",
"sizeAggregation": "Sum",
"opacity": 0.8,
"labelSettings": "friendly_location",
"legendMetric": "FailureCount",
"legendAggregation": "Sum",
"itemColorSettings": {
"nodeColorField": "FailureCount",
"colorAggregation": "Sum",
"type": "heatmap",
"heatmapPalette": "greenRed"
}
}
},
"name": "query - 0"
}
-
Paste the json code inside the query window
-
Save the Map generated